Digital Ocean Private Networks¶
Digital Ocean has the ability to allow Droplets to communicate over a private network. Digital Ocean
does this over a separate interface. In order to use this interface and allow UH VPN
clients to reach Droplets over the private network, iptables rules need to be added.
Step 1: Determine the private subnet¶
First login to the Digital Ocean control panel navigate to a Droplet using private networking, click on the “Networking” or “VPC” tab and scroll down to the “Private Networking” section:

In the image above the private network is 10.106.0.0/20. Note yours down as it’ll be used later.
Step 2: Add iptables rules¶
Digital Ocean uses a separate interface for private networking and so the default NAT rule inserted by the UH VPN server does not cover the private subnet. To rectify this one must first SSH into the Droplet and determine the interface used for the private network by executing the command:
route

In the above example, it is possible to see that the eth1 interface is used by Digital Ocean
for the network 10.106.0.0/20.
Next it’s time to add the appropriate iptable rule. In order to do this one must first know the
tunnel network used on the UH VPN Server. To obtain this head over to the UH VPN website and
within the relevant group click the next to the server in question. Then note down
the tunnel network.
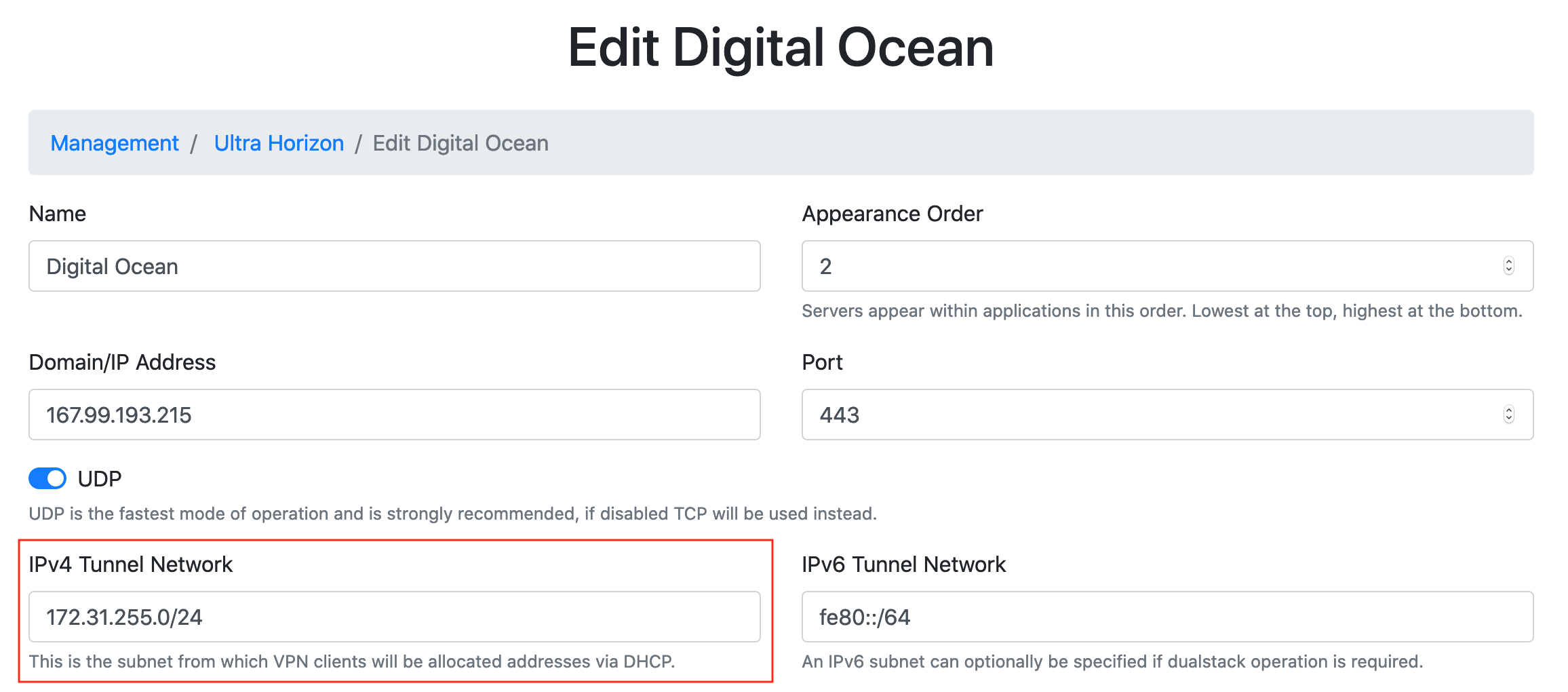
In the above example, the tunnel network is: 172.31.255.0/24
Finally, to enable connectivity from UH VPN clients to the Digital Ocean private network execute the following command:
iptables --table nat --append POSTROUTING -s 172.31.255.0/24 --out-interface eth1 -j MASQUERADE
where 172.31.255.0/24 and eth1 are replaced with your own tunnel network and interface
respectively.
At this point one should attempt to connect to the UH VPN Server and check to ensure that connecting clients are able to reach other Droplets within the private network.
Step 3: Ensure persistent reboots¶
iptables commands are not persistent across reboots. This means that every time a server is rebooted,
the rule providing connectivity to the private network is removed. To avoid this problem, it is necessary
to insert the iptables command used above into /etc/rc.local so that it is executed on boot.
To do this first edit the file /etc/rc.local:
nano /etc/rc.local
Then add the command you used above into the file along with the shebang line (#!/bin/bash):
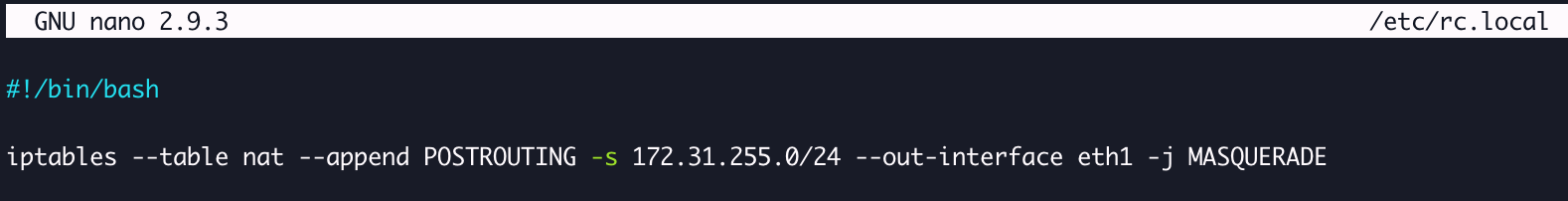
Then save the file (Ctrl-X) in nano. This will ensure that the rule is inserted every time the server is booted. Then finally make sure the script is executable:
chmod +x /etc/rc.local
Note
It is imperative that you update this rule in /etc/rc.local if you change the tunnel
network in the UH VPN Server settings.
Enterprise Enhancements¶
It is quite common for cloud users to only want traffic destined for the Digital Ocean private network to be routed over the VPN instead of their entire Internet connection. This is to avoid extra charges from Digital Ocean if bandwidth/data exceeds the monthly allowance.
This can be easily accomplished via UH VPN’s custom IP routing (an enterprise licence feature). To enable this
functionality head over to the website and within the relevant group click the
next to the server in question.
Ensure that both switches, “Redirect all IPv4 Traffic” and “Redirect all IPv6 Traffic” are switched off, then proceed to add your Digital Ocean private network into IPv4 selection box and leave the IPv6 selection box blank. In addition, leave the “DNS Servers” field blank unless you wish to send DNS traffic to an IP on the Digital Ocean private network:

Turn off the “Add NAT Rule” switch.
Then save the server. Once this is done, connecting clients will only be pushed the routes for the Digital Ocean private network.